ISSessions CTF 2024 - OSINT
This is a continuation of my walkthrough; the main post is found here
OSINT (Open Source Intelligence) is always a fun category, akin to a quiz show style, but works on the premise of using publicly accessible information to find the solutions to riddles or focus on techniques that real-life attackers might use. For instance, in one CTF, it was taking a blurry photo of a plane utilizing the small details you could see and then figuring out the owner of it based on the blurry tail colors and rough logo shape, how many engines, and roughly where the photo was taken. One important thing people often forget nowadays is that the information we put out there can be used against us either through a targeted password brute force attempt or what people often don't protect nearly as well, the answer to their secret questions, which often with little to no verification will reset your account access.
This was my first category; it helps set a flow going forward.
Code Name
Clue:
I am known for giving vital information!
I created anti-aircraft weapons systems for specific military.
I am considered a traider by my government but i am not. I am known for a specific code name do you know?
Picture:

Looking at the picture and seeing that it would be in an archive, I used my snipping tool to crop out only the head and put it through Google Photos' reverse search. It came back to the name Adolf Tolkachev, and since they were looking for a code name, I continued searching till I got GT/VANQUISH. Trying that still didn't work, so continuing in the search, I found a book called The Billion Dollar Spy. It had a review under it, which referenced another code-named CKSphere.
https://www.amazon.com/gp/aw/review/0345805976/R85YJNAQPLKFS
This was correct now: EspionageCTF{CKSPHERE}
Where are you
Clue:
I have to know where he took this picture, I need to know what street that is (For the flag swap spaces with underscores “_”)
Picture:

Looking at the photo, one thing that stood out to me was the Empire State Building. And the TD back directly to the right. Doing a quick Google search for TD banks near the Empire State Building narrowed the choices to 1 with the right viewing angle, which got us to 40.74846632266793, -73.9888155231253, which gave us W 32nd St.
This was correct now: EspionageCTF{W32ndSt}
Bitcoin Case
Clue:
The Feds received a tip of a bitcoin address the address is 14hVKM7Ft2rxDBFTNkkRC3kGstMGp2A4hk.
You are tasked with determining the following:
Can you identify what type of malware this is and who it belongs to?
IMPORTANT
***Do not download the file!!!!***
This one was actually pretty easy. Simply searching the bitcoin wallet and the keyword bitcoin brought up all the information required to answer it.
https://www.malwarebytes.com/blog/detections/ransom-ryuk or the link in the top 10 described it enough.
The Correct answer: EspionageCTF{Ransomware_Ryuk}
History
Clue:
I was created with good intentions! I was made with one goal in mind to destroy a facility. I was created in a national laboratory.
What is my name?
This was another one I found decently easy. Simply by reading it, I already had the answer as Stuxnet was created to attack the nuclear enrichment centrifuges.
Answer: EspionageCTF{Stuxnet}
Boat Dock
Clue:
I am hiking at this location 54.6436540065792, -129.76707688328335. My boat is anchored close by.
My gps has stopped working i need to make it back before night i remember there is a marina roughly 44km away.
Can you tell me the name of the village that the marina is located in?
So first, we have the coordinates we can check, but we are also given a rough distance of 44km away to find nearby. With this challenge, what was funny was how many different ways I tried to measure using the distance key until I realized you could easily measure between two points after a quick Google search. Before that, I was trying docks in the area.
Looking it up online, the coordinates 54.6436540065792, -129.76707688328335 return to Khutzeymateen Grizzly Bear Sanctuary. Using the measuring tool,
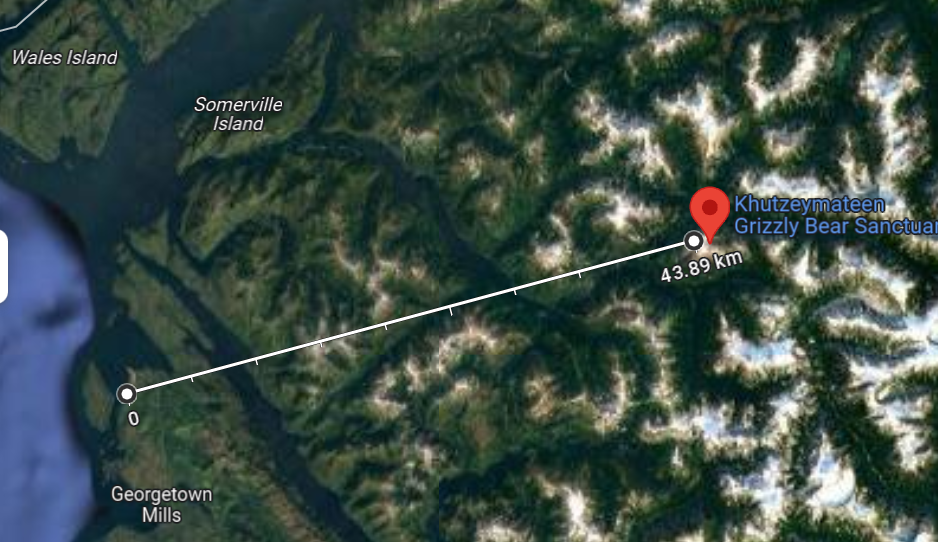
Answer: EspionageCTF{Lax_Kw'alaams}
What was funny about this one was how much difficulty I had with Google Maps, which made it take way longer than it should have. After that, realizing the space was filled with an underscore was more so the last "challenge."
PGP
Clue:
Can you tell me who the owner is of this pgp key?
Provided Key:
-----BEGIN PGP PUBLIC KEY BLOCK-----
mDMEZWKrNhYJKwYBBAHaRw8BAQdAlU3YHDemI0njRHNWOr131q/5QTQ+2UUjzK2Z
vPz4zdu0GkRlYnJhX1NweSA8RGVicmFAdGVzdC5jb20+iJkEExYKAEEWIQTLHgaK
djk/naz50EjMLZ06KbaoJQUCZWKrNgIbAwUJBaSTCgULCQgHAgIiAgYVCgkICwIE
FgIDAQIeBwIXgAAKCRDMLZ06KbaoJcFjAP9B9yoQ7gU4MwGb+l1yFJeUbv0W2ZAL
XzlU4yirk0kE6wEAwXDVKIbJOE8fT0JCVyFB/cWUFx9VxpCFCvDpEe3vRAe4OARl
Yqs2EgorBgEEAZdVAQUBAQdAGSLnD323aYpXSF9uQ7G8DnYfOz14Gc9Pk0jDxpR+
Yn4DAQgHiH4EGBYKACYWIQTLHgaKdjk/naz50EjMLZ06KbaoJQUCZWKrNgIbDAUJ
BaSTCgAKCRDMLZ06KbaoJSyzAP9VnNzVS+ICopJ0uCHUjUDBo126kfWyXF4Be/eF
VnzpnwD/RLYimbfbSY2mlIyoxpjgf9W9dwB99HgOf/MKPpVO+gY=
=foST
-----END PGP PUBLIC KEY BLOCK-----
This was an interesting challenge because at the time I hadn't setup my Linux VM so I instead went on a bit of a hunt on the internet for a browser-based decoder which I found at:
https://cirw.in/gpg-decoder/
Entering the key gave us the information
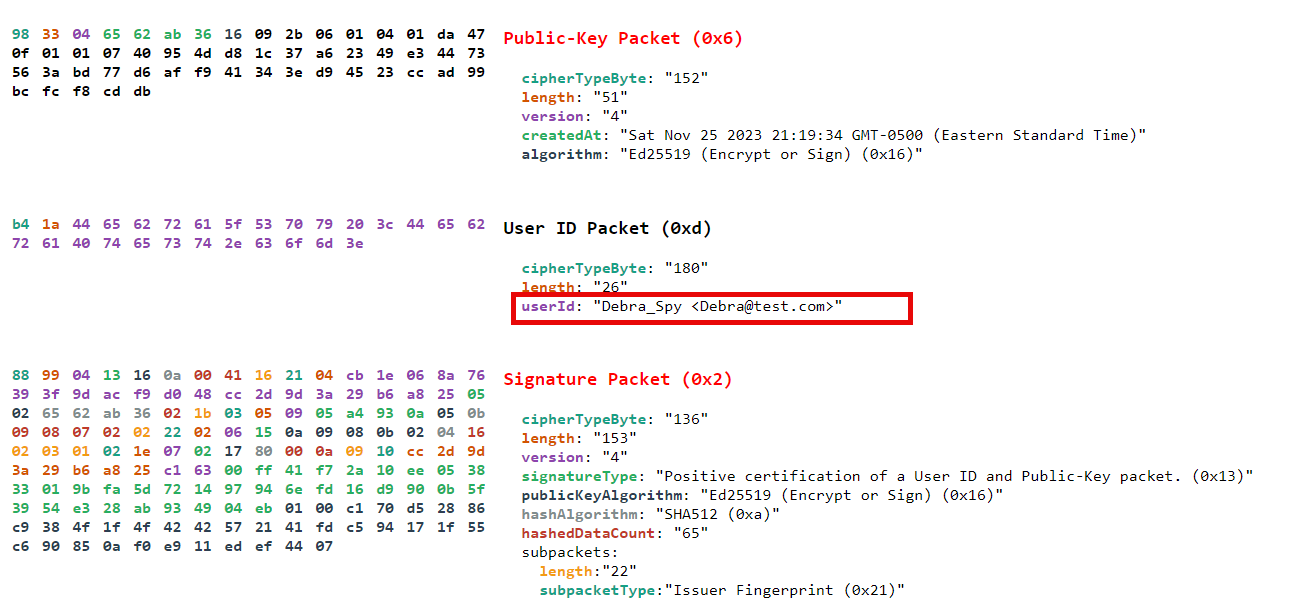
The owner was Debra Spy
The Answer: EspionageCTF{DebraSpy}
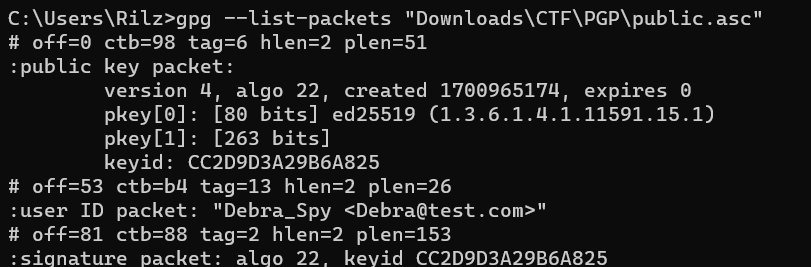
After finishing the challenge, I also realized from an algorithms course I actually had GPG installed on my laptop and was also able to view it using the command.
gpg --list-packets
Totally A Virus
Clue:
We're investigating a ransomware case on one of our systems. The perps left a note, we want you to find more info about this file. Perhaps if it's been observed with any other names?
File: ransom_note.txt
At first, looking at this, I tried searching up some key phrases; I looked at the ASCII Art to see if there were any patterns around, none of which yielded any results. In the end, I left this challenge for a few hours and after dealing with a few hashes, I had an idea to take the hash and toss it into Virus Total. While this isn't specifically anything top secret, creating the hash and checking that way is always an ideal way not to have a machine connected to the internet with what you suspect is malware.
Using the command in a Powershell terminal as I was on Windows
Get-FileHash ./ransom_note.txt
This provided us with a SHA256 hash of F2ED1E76C38219E59BC53B11293DF3591E58AB3C3C6ACA482AC3D649BF1D7E92
This allowed us to simply plug the hash into the site without disclosing the file. The useful thing about the site is it lets you know other files it is known for, which happened to be where the flag was hiding.
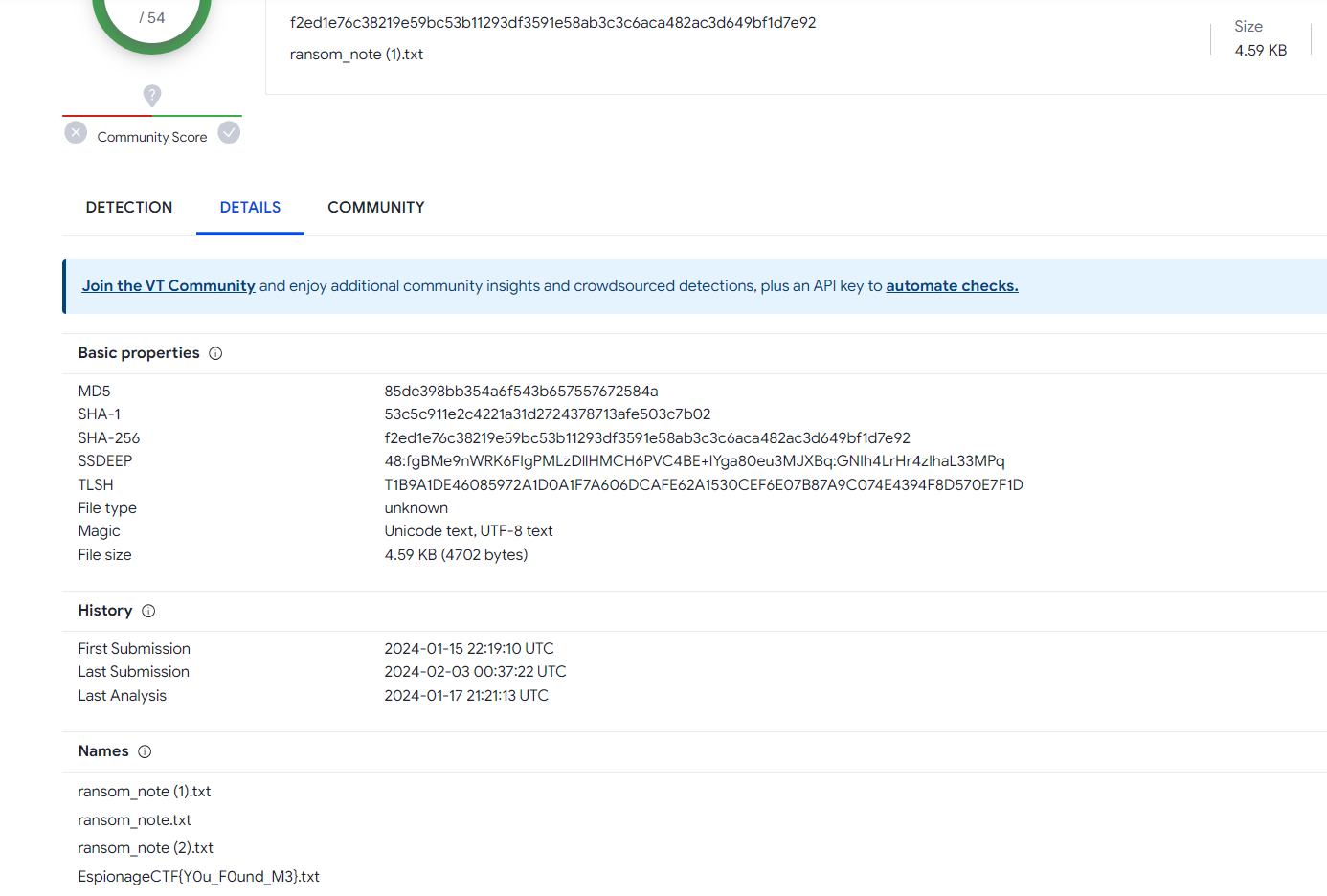
The Answer: EspionageCTF{Y0uF0undM3}